Even McDonald's thinks you need to change your passwords - especially if they're burger-related
McDonald’s campaign uses humorous ways to draw attention to poor password habits

Sign up for breaking news, reviews, opinion, top tech deals, and more.
You are now subscribed
Your newsletter sign-up was successful
- Passwords tied to fast food remain common in over 110,000 breaches
- Substituting letters with symbols no longer protects accounts from automated attacks
- Reusing weak passwords continues to threaten both individual and enterprise security
Despite years of cybersecurity advice and pressure, many internet users continue to rely on easy-to-remember passwords related to popular foods.
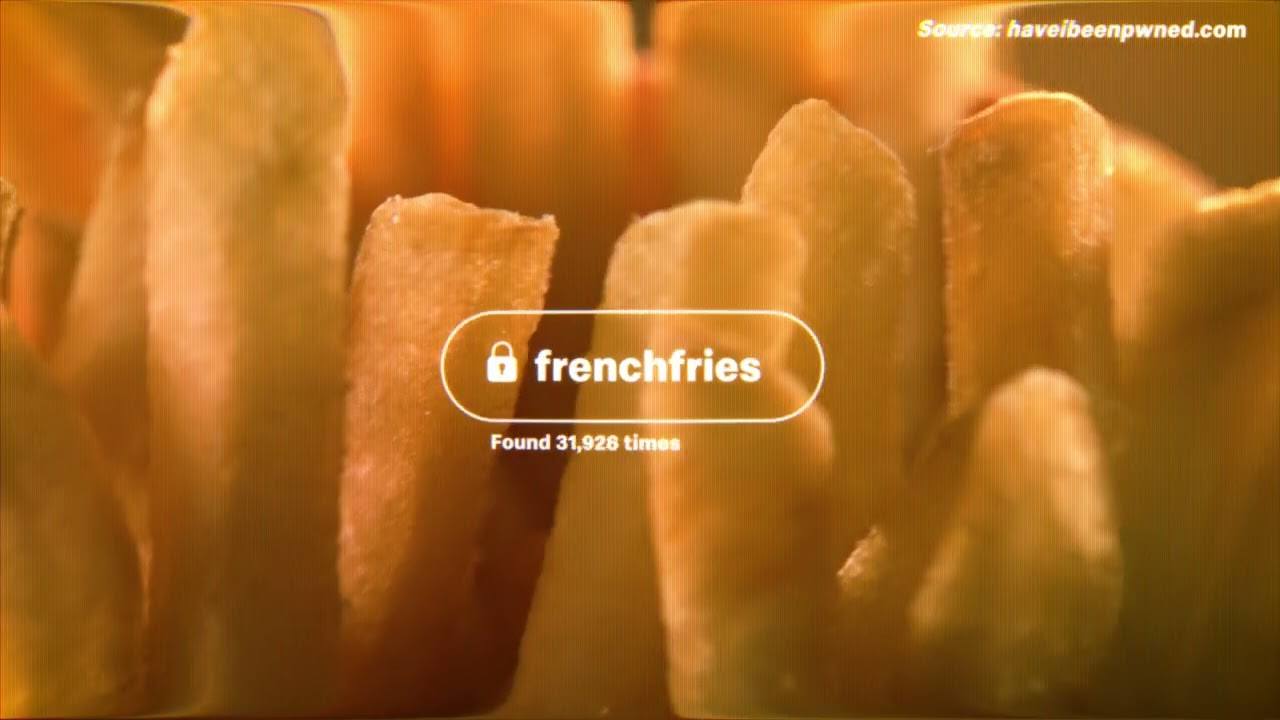
A new report from McDonald’s has revealed common passwords such as “bigmac,” “happymeal,” and “mcnuggets” appeared in more than 110,000 compromised accounts, according to data from Have I Been Pwned.
Variations that use basic character substitutions appear just as frequently, indicating that familiarity continues to outweigh caution for many account holders.
Substitutions no longer help
McDonald’s campaign, including posters and short videos, relies on humor and recognition to reach a broad audience.
The message is straightforward: passwords tied to popular food items are easy to guess and widely abused.
Replacing letters with symbols or numbers once added meaningful resistance against basic attacks, but this approach no longer protects against modern cracking methods.
Automated tools already account for predictable substitutions and routinely test them during brute-force attempts, as when a password begins with a common word, attackers need little effort to cycle through known variations.
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
The persistence of these habits shows that awareness campaigns have had limited impact outside technically inclined circles.
Security providers frequently recommend long passphrases, multi-factor authentication, and automated credential storage, but despite this guidance, many users continue to treat passwords as the sole line of defense.
Even younger users, who are more familiar with modern security tools, often reuse weak passwords across services.
Enterprises encounter the same issue internally, where administrative accounts occasionally rely on simple credentials despite formal policies.
This disconnect explains why basic password hygiene remains a recurring issue decades after it first surfaced.
While the approach draws attention, it does not address the structural reasons weak passwords persist, including convenience and resistance to change.
Public reminders may reduce the most obvious examples, but they rarely shift behavior without supporting tools.
This is a wake-up call for users who still think a weak password is enough. If users do not know how to create a strong password, a password generator can create long, random credentials that do not depend on recognizable words.
Password managers can help users store those credentials securely without requiring them to remember each one.
In organizational environments, a business password manager centralizes control, reduces reuse, and limits damage when breaches occur.
Via The Register
Follow TechRadar on Google News and add us as a preferred source to get our expert news, reviews, and opinion in your feeds. Make sure to click the Follow button!
And of course you can also follow TechRadar on TikTok for news, reviews, unboxings in video form, and get regular updates from us on WhatsApp too.

Efosa has been writing about technology for over 7 years, initially driven by curiosity but now fueled by a strong passion for the field. He holds both a Master's and a PhD in sciences, which provided him with a solid foundation in analytical thinking.
You must confirm your public display name before commenting
Please logout and then login again, you will then be prompted to enter your display name.